Permissions dictate the actions users can perform on a system, determining access levels and restrictions. Permissions are essential in ensuring that users have appropriate access to resources while maintaining security.
In today’s digital age, where data privacy and security are paramount, understanding permissions is crucial for businesses and individuals alike. By properly setting permissions, organizations can prevent unauthorized access to sensitive information, reducing the risk of data breaches and cyber threats.
Moreover, permissions play a key role in compliance with regulations such as GDPR and HIPAA. We will explore the importance of permissions, common types of permissions, and best practices for managing permissions effectively. Let’s delve into the world of permissions and empower you with the knowledge to safeguard your digital assets.
Credit: developers.google.com
What Are Permissions?
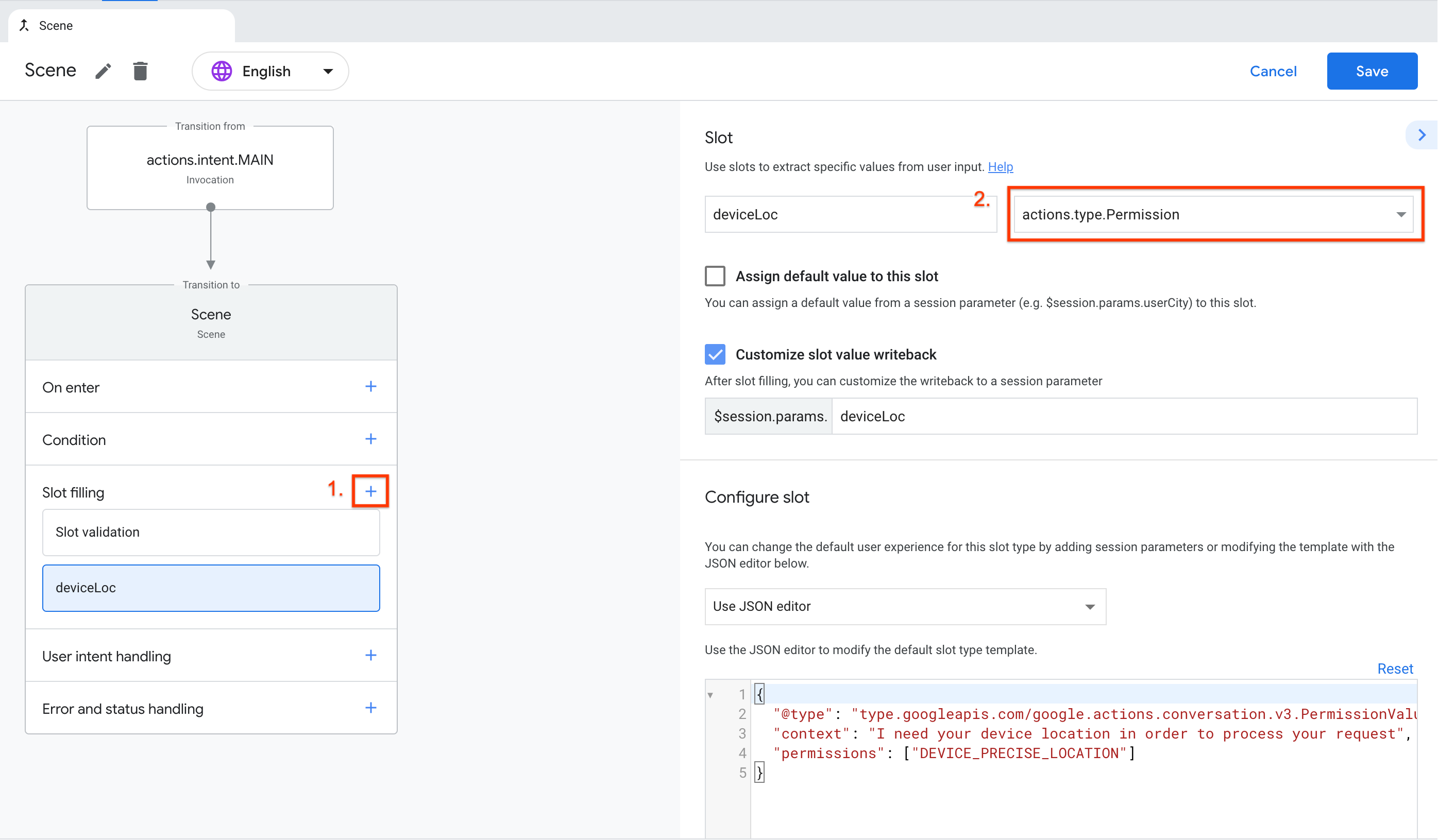
In the digital world, permissions play a crucial role in ensuring the security and privacy of data. Understanding permissions is essential for website owners, administrators, and developers. So, what are permissions? Let’s delve into the details to gain a comprehensive understanding.
When it comes to digital assets, there are various types of permissions that dictate access rights. These include:
- Read
- Write
- Execute
Each type of permission is essential for controlling the level of access users have to certain files and directories.
Permissions play a crucial role in digital security by regulating access to sensitive information. By defining who can read, write, or execute certain files and directories, permissions maintain the integrity and confidentiality of data. Additionally, they contribute to the overall control and management of digital assets, ensuring that only authorized individuals have access to specific resources.
Types Of Permissions
Permissions are crucial in determining what actions users can perform on a system. There are various types of permissions that govern access control.
Read Permission
Allows users to view the contents of a file but does not grant the ability to modify or delete it.
Write Permission
Enables users to modify the contents of a file, including the ability to add, edit, or delete information.
Execute Permission
Grants users the authority to run a file as a program or script, executing its commands or functions.
Role Of Permissions
Permissions play a crucial role in maintaining the security and integrity of data within a system. By assigning specific permissions to users based on their roles and responsibilities, organizations can ensure that sensitive information is safeguarded from unauthorized access.
Ensuring Data Security
Permissions help in protecting sensitive data from unauthorized access, reducing the risk of data breaches and ensuring compliance with regulatory requirements.
Controlling Access Levels
By defining access levels through permissions, organizations can control who can view, edit, or delete specific data, minimizing the chances of data tampering or unauthorized modifications.
Maintaining System Integrity
Permissions play a key role in maintaining the overall integrity of a system by regulating user actions, preventing accidental or intentional damage to critical system components.

Credit: support.wix.com
Setting Permissions
Setting permissions is a crucial part of managing access to files and directories on a computer system. It involves defining who can access what and what actions they can perform. In this section, we will delve into the different types of permissions and how they can be set up in a system.
User-based Permissions
User-based permissions are specific to individual users. Each user is assigned distinct permissions that govern their access to files and directories. When setting user-based permissions, the system administrator can define which files a particular user can access and the actions (such as read, write, or execute) they can perform on those files.
Group-based Permissions
Group-based permissions are assigned to a group of users. This approach simplifies the process of managing permissions for multiple users who require similar levels of access. By categorizing users into groups, the administrator can set permissions for the entire group at once, improving efficiency and security.
Default Permissions
Default permissions are the access rights automatically assigned to new files and directories when they are created. By setting default permissions, the system administrator ensures that newly created files and directories inherit the specified access rights, streamlining the overall permission management process.
Handling Permission Issues
Permissions play a crucial role in ensuring the proper management and security of files and data. However, handling permission issues can sometimes be a challenging task. Whether it’s troubleshooting access problems or granting and revoking permissions, addressing these issues promptly and effectively is essential. In this section, we will explore some common permission problems and discuss strategies to overcome them.
Troubleshooting Access Problems
Access problems can arise when users are unable to view or edit certain files or folders. These issues can be frustrating, but with a systematic approach, most access problems can be resolved. Here are a few troubleshooting steps to consider:
- Check the user’s role and permissions: Ensure that the user has the necessary role and specific permissions assigned to access the file or folder.
- Verify file and folder permissions: Review the file and folder permissions to ensure they allow the desired level of access. Make sure there are no conflicting permissions.
- Confirm user group membership: Users may experience access problems if they are not part of the correct user group. Verify that the user is assigned to the appropriate group.
- Check file and folder ownership: Ownership of files and folders can affect access. Make sure the user has the necessary ownership or is granted permission through group ownership.
- Identify potential conflicts: Evaluate if there are any conflicting permissions or settings that may be causing access issues. Resolve any conflicts to restore access.
Granting And Revoking Permissions
Granting and revoking permissions is an essential administrative task that allows users to manage resources effectively. Here are some key points to consider:
- Analyze the required permissions: Determine the specific permissions needed for a user or group. Grant only the necessary permissions to avoid potential security risks.
- Use groups to manage permissions: Assign users to appropriate groups based on their roles and responsibilities. This simplifies permission management for multiple users.
- Regularly review and audit permissions: Periodically review and audit permissions to ensure they align with changing roles and responsibilities. Remove unnecessary permissions to maintain a secure environment.
- Document permission changes: Keep a record of permission changes for reference and accountability.
By following these best practices, you can effectively handle permission issues and maintain a reliable and secure file management system.

Credit: android-developers.googleblog.com
Frequently Asked Questions For Permissions
How Do I Find My Permissions?
To find your permissions, go to the settings or preferences section of the platform or software you are using. Look for the “Permissions” or “Privacy” tab, where you can view and manage the permissions granted to your account.
How Do I Enable Permissions In Google?
To enable permissions in Google, go to the “Settings” of your account. Click on “Privacy & Security” and then “Permissions. ” Here you can manage access for various apps and services.
How Do I Set Up Permissions?
To set up permissions, navigate to the settings menu, select “Permissions,” and adjust access levels for users.
How Do I Remove Permissions From Google?
To remove permissions from Google, go to your Google account settings. Select the app or service and click on the “Remove Access” option.
Conclusion
Understanding permissions is crucial for maintaining security and controlling access to information. By implementing effective permission systems, organizations can safeguard their data and ensure that only authorized individuals can access it. With the right approach to permissions, businesses can enhance their cybersecurity posture and minimize the risk of unauthorized access or data breaches.


